When moving to Office 365 you haven't just got the mailbox data to worry about, but also a variety of other issues like ensuring your on premise configuration and policies are understood and carried over to Exchange Online.
In a Cutover, Staged, Hybrid or third party migration you may want to prep many policies prior to moving the first mailbox to Office 365.
One of the policies you may want to configure prior to moving the first mailbox is
Activesync Mailbox Policies. If you have many policies, auditing them and then creating them in Office 365 can be a time consuming task. Luckily I have written a script to help with this.
The script will do the following actions:
Check to see if any of your policies has a null field for the password device length. This should be between 1 and 16. If any are indeed null the script will inform you the policies that are at fault and halt
Export all of your Activesync Mailbox policies (including your default policy if you include –ModifyDefaultPolicy) – it will create local files from where the ps1 file is run from
Connect to Exchange Online in the powershell session (it will prompt for username and password)
Create all Activesync Mailbox policies with the on premises names and configuration settings
Clean up any local files it created when performing the export process
Disconnect any powershell sessions it has open
Inform you the process has completed successfully.
The script works well, but it is designed to be used prior to moving the first mailboxes, not that it will cause an issue if it is ran later than that of course, but because an Administrator may have already started to make changes or even set up policies using the same names as the on premise ones.
If you do run into this condition it will simply fail on creating that policy, similarly if you run the script again it will complete successfully but will fail on creating new policies as they are already created.
If you have decided to include the –ModifyDefaultPolicy switch it will also gather your default policy settings and then export them and configure the existing Office 365 default policy with the settings it has exported.
Let's take a look at it in action. Logging onto my new Office 365 tenant I can see I just have the default policy with default out of the box settings:
If I look at my on premise configuration you can see I have multiple Activesync Mailbox policies in use:
Each policy has different configuration settings. You can see in the Office 365 EAC my default policy is set with default settings and doesn't require a password. However my on premise default policy does with a minimum password length of 6 characters:
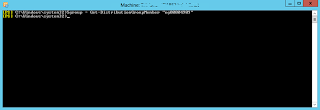
I have opened a Powershell session and I will run .\ImportEASPolicies2EXO.ps1 –ModifyDefaultPolicy
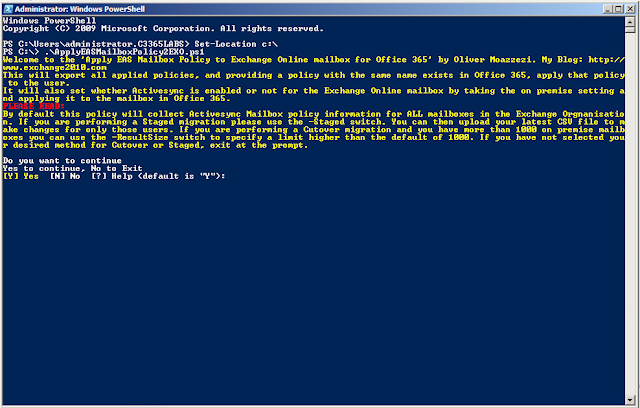
It will first check to see if there are any policies with an incorrect, or null, password length and advise you of them:
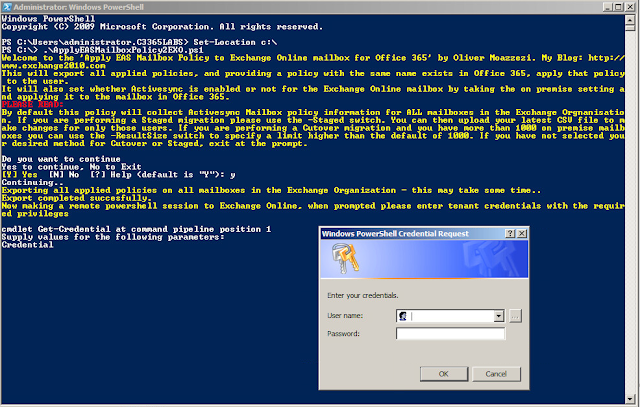
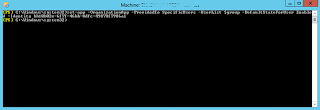
Providing that is fine, it will continue and export the on premise policies before making a connection to Exchange Online. It will prompt for your tenant credentials:
Once connected it will start creating the policies, and modify the default policy if you selected to do this (like I am in my example):
Once completed you can close the window. It will disconnect any PS Sessions it has created and also clean up any files created during the process.
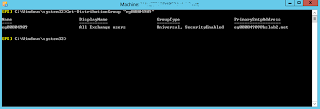
So let's take a look back in the Office 365 tenant EAC
You can see the policies have been created and the Default policy has been modified successfully.
Once the *-ActivesyncMailboxPolicy cmdlets no longer work I will update the script to a version 2 making use of *-MobileDeviceMailboxPolicy. But this won't be for some time.
Until that time using the older cmdlet makes things easier.
You can grab the script
HERE.
Have fun!
Oliver Moazzezi – MVP Exchange Server