Azure Conditional Access is a policy and access enforcement solution for both Azure and Office 365 services. Conditional Access requires Azure AD Premium P1 or above before it's available to be configured on your tenant.
Microsoft are currently moving conditional access to the new Azure portal experience https://portal.azure.com where it is in Preview. So I thought I would compare the old and new experience and post it here.
On top of this location and experience change they have also enabled far more granular policy controls for granting access to services as well as expanding support for Office 365 workloads. Which is great news to hear. We can now specify conditional access for Skype for Business online.
First off though, let's look at the legacy portal experience at https://manage.windowsazure.com
Once logged in select your directory
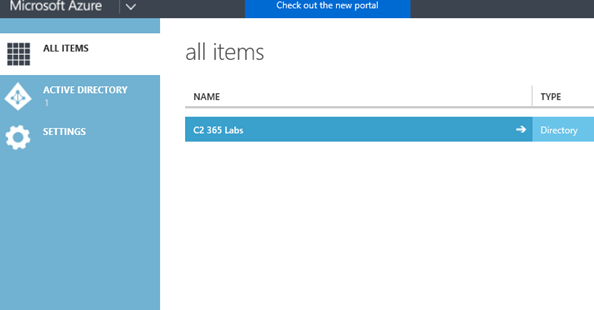
From here we browse to 'Applications'
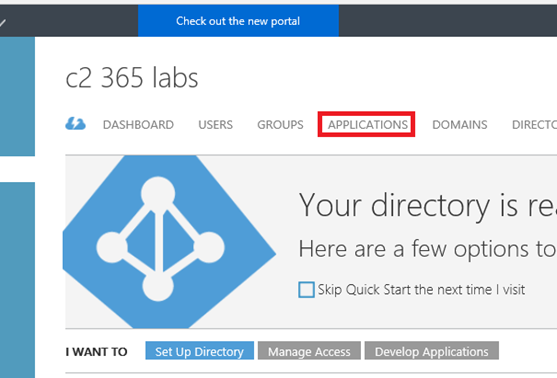
Select your workload, in this example I have selected 'Exchange Online'
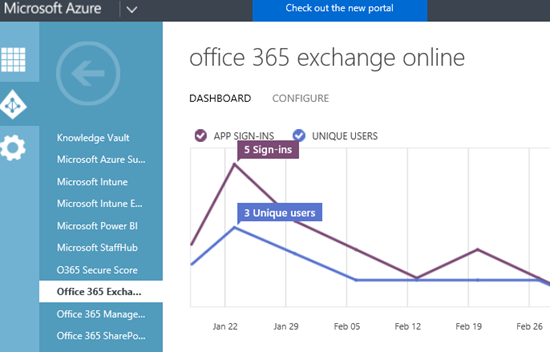
We then have the option of enabling access rules for 'multi-factor authentication and location based policy control, and device based policies.
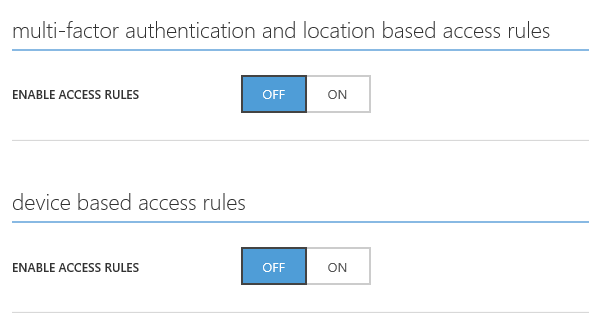
Once enabled we can specify rules that effect all users - or concentrate them on a specific group - and include exclusions if necessary.
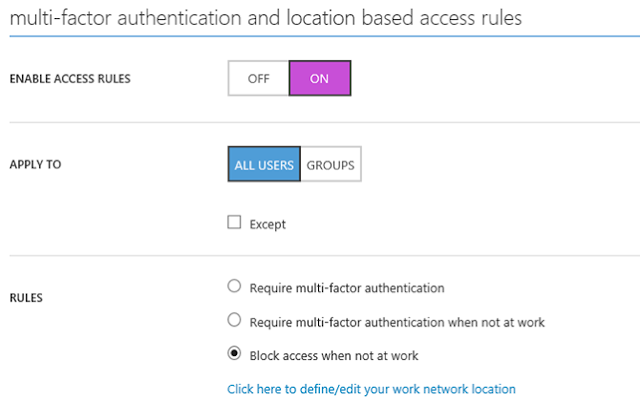
In this example I am specifying a policy based on specific groups
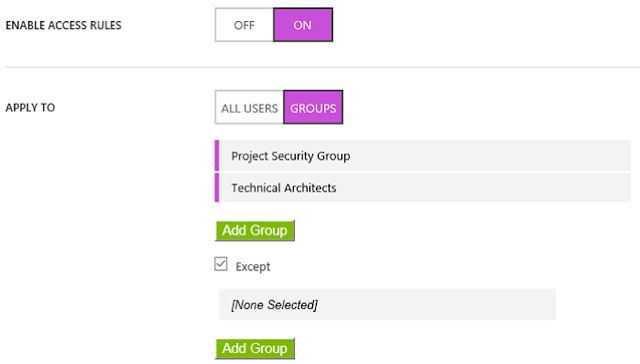
And blocking access when a user is not at work (or allowed network).
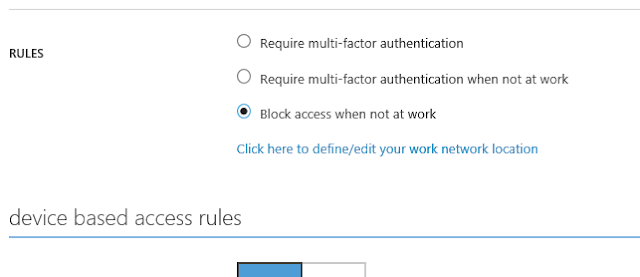
To define your network locations, select 'define/edit your network location' and enter your public IP subnets that should be trusted.
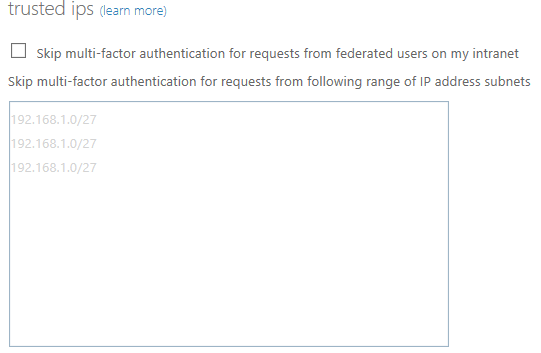
Once back at the rule, ensure you save your selection

Should I wish to enable device access, I simply enable this also
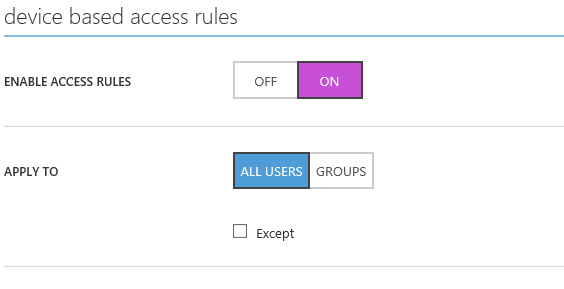
Specify whether I want all devices in scope or specific ones
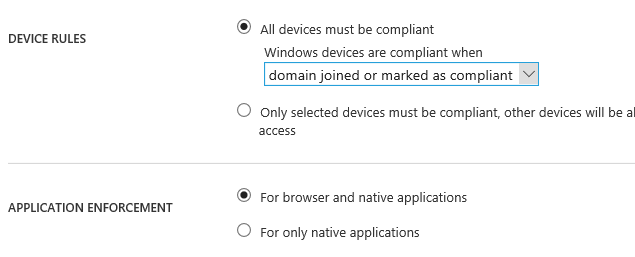
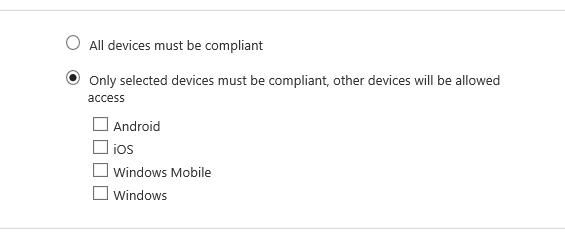
if I am being specific then selecting which OS/device this is
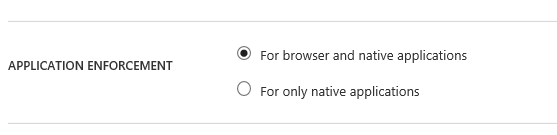
And then deciding if this is for the browser and native applications or native applications only
And the result of this rule? Being denied access to Exchange Online as I do not meet the conditional access criteria
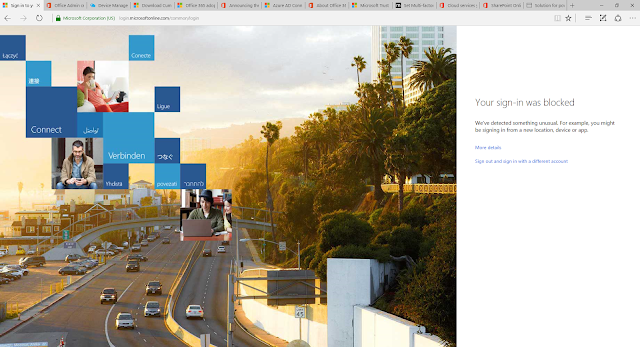
So how does Azure Conditional Access Preview compare?
For users not used to the new Azure Portal you may at first need time to work out how the interface works.
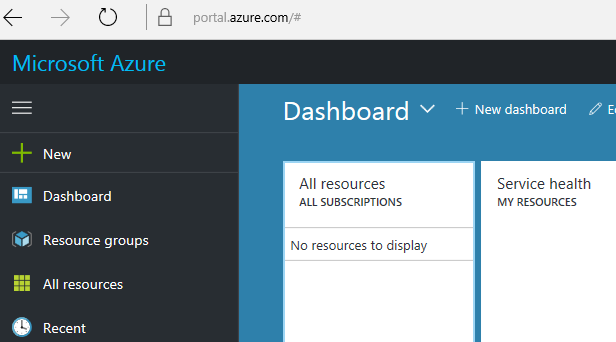
Once logged in, select Azure Active Directory on the left pane
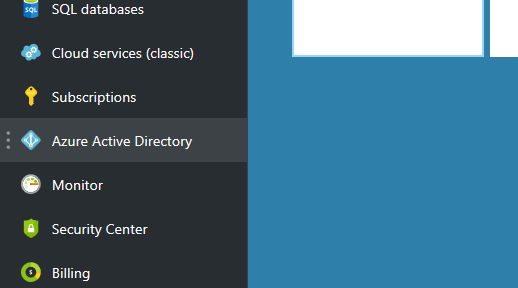
Once within Azure Active Directory, select Conditional Access
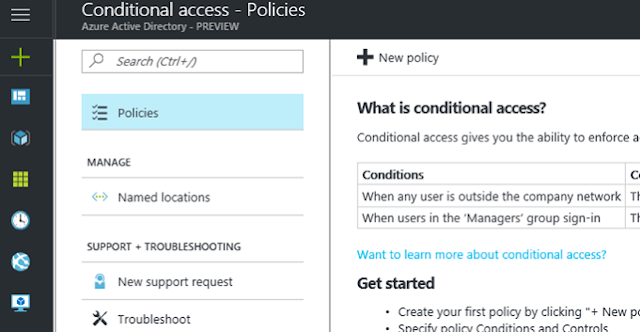
At this moment in time, if you have policies already configured in the legacy portal you cannot see them here. I am sure once out of Preview Microsoft will be looking to migrate your existing policies. For greenfield select 'New Policy'
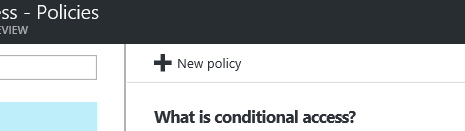
Select a name for your policy. We then work our way through the assignment section, this specifies Users and Groups, Cloud Apps and Conditions
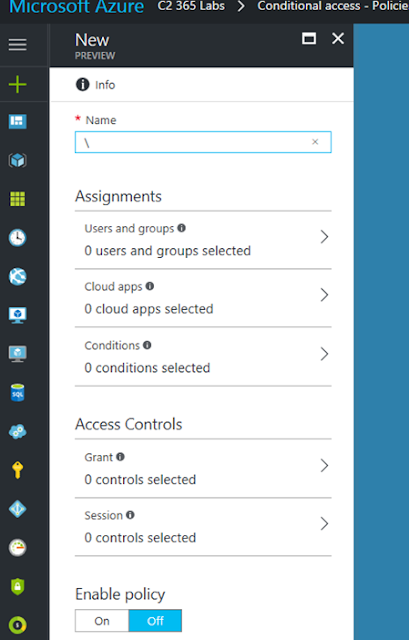
Specify if the policy is for all uses or groups, exclusions are still possible on the seperate tab
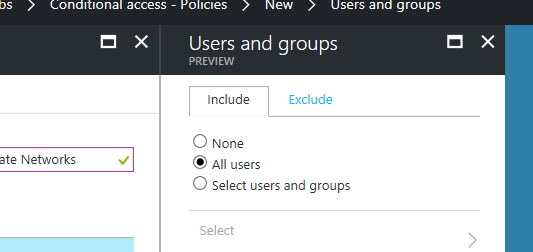
We can now multi select our cloud apps and create policies for multiple workloads
Now we have specified our users or groups, and cloud apps, we move on to the conditions for access
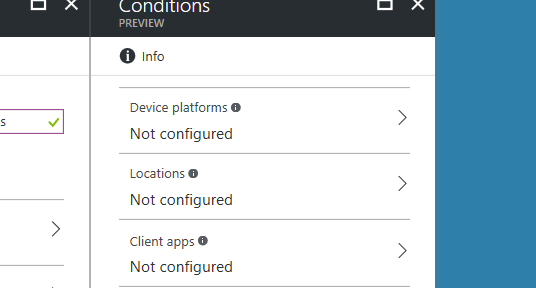
Device based access, multi factor enforcement and location based access are all rolled into one. The Preview still honours your Trusted IPs - and infact you must still configure them in the same place as previously shown.
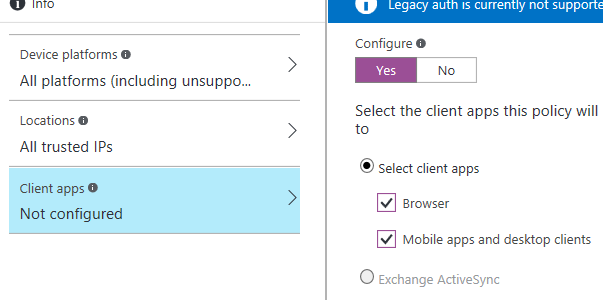
You will find the Preview has far more granular control for fine tuning your conditional access requirements
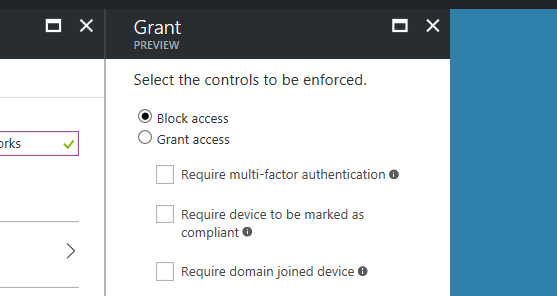
We then enable the policy, the policy goes through validation checks and then is immediately enforced
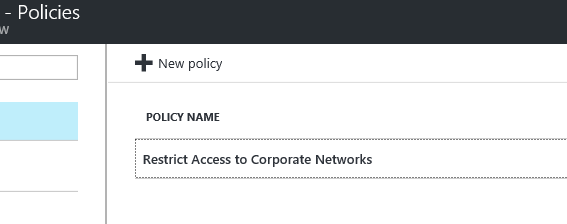
We receive the same conditional access user experience
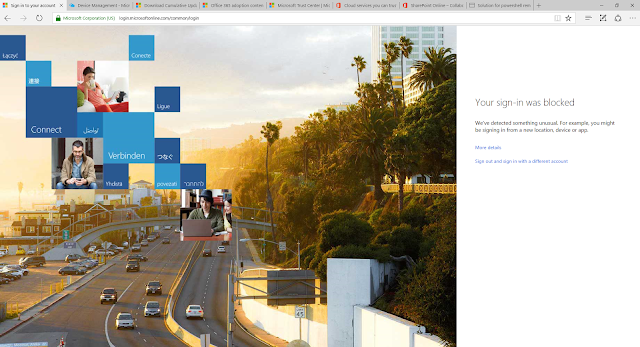
Keeping in mind the new experience is still in Preview - and you won't want to necessarily move over just yet - I would recommend looking at the new portal experience and start to plan how you will possibly add additional benefits to your conditional access policies that you may not have had the granular ability to do so before - or indeed the support for a particular service.
It will also provide you with the familiarity of the new portal experience.
Enjoy,
Microsoft are currently moving conditional access to the new Azure portal experience https://portal.azure.com where it is in Preview. So I thought I would compare the old and new experience and post it here.
On top of this location and experience change they have also enabled far more granular policy controls for granting access to services as well as expanding support for Office 365 workloads. Which is great news to hear. We can now specify conditional access for Skype for Business online.
First off though, let's look at the legacy portal experience at https://manage.windowsazure.com
Once logged in select your directory

From here we browse to 'Applications'

Select your workload, in this example I have selected 'Exchange Online'

We then have the option of enabling access rules for 'multi-factor authentication and location based policy control, and device based policies.

Once enabled we can specify rules that effect all users - or concentrate them on a specific group - and include exclusions if necessary.

In this example I am specifying a policy based on specific groups

And blocking access when a user is not at work (or allowed network).

To define your network locations, select 'define/edit your network location' and enter your public IP subnets that should be trusted.

Once back at the rule, ensure you save your selection

Should I wish to enable device access, I simply enable this also

Specify whether I want all devices in scope or specific ones

if I am being specific then selecting which OS/device this is

And then deciding if this is for the browser and native applications or native applications only

And the result of this rule? Being denied access to Exchange Online as I do not meet the conditional access criteria

So how does Azure Conditional Access Preview compare?
For users not used to the new Azure Portal you may at first need time to work out how the interface works.

Once logged in, select Azure Active Directory on the left pane

Once within Azure Active Directory, select Conditional Access

At this moment in time, if you have policies already configured in the legacy portal you cannot see them here. I am sure once out of Preview Microsoft will be looking to migrate your existing policies. For greenfield select 'New Policy'

Select a name for your policy. We then work our way through the assignment section, this specifies Users and Groups, Cloud Apps and Conditions

Specify if the policy is for all uses or groups, exclusions are still possible on the seperate tab

We can now multi select our cloud apps and create policies for multiple workloads

Now we have specified our users or groups, and cloud apps, we move on to the conditions for access

Device based access, multi factor enforcement and location based access are all rolled into one. The Preview still honours your Trusted IPs - and infact you must still configure them in the same place as previously shown.

You will find the Preview has far more granular control for fine tuning your conditional access requirements

We then enable the policy, the policy goes through validation checks and then is immediately enforced

We receive the same conditional access user experience

Keeping in mind the new experience is still in Preview - and you won't want to necessarily move over just yet - I would recommend looking at the new portal experience and start to plan how you will possibly add additional benefits to your conditional access policies that you may not have had the granular ability to do so before - or indeed the support for a particular service.
It will also provide you with the familiarity of the new portal experience.
Enjoy,
|



