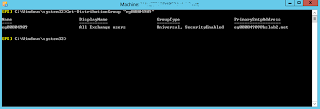
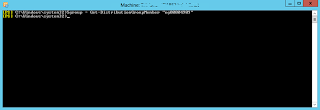
Microsoft launched the CSP at The Microsoft WorldWide Partner conference in 2014, but only now the fruits of Microsofts efforts are starting to be seen in Office365.
You have to qualify to be considered as a CPS partner, but qualification doesn't automatically mean acceptance yet – for the time being you must be accepted also.
There are currently 2 tiers to the CSP, outlined below.
1-Tier is the program of choice for partners looking to provide an end-to-end customer experience, including customer support. In this model, the partner has a direct relationship with Microsoft. This program requires partners to have high capability standards to provide a great customer experience.
2-Tier is designed for resellers to work with their 2-Tier distribution partners to sell Microsoft cloud services. In this program, the 2-Tier distribution partner provides reseller and customer support. Most partners will participate in the CSP program as a 2-Tier reseller
2-Tier is designed for resellers to work with their 2-Tier distribution partners to sell Microsoft cloud services. In this program, the 2-Tier distribution partner provides reseller and customer support. Most partners will participate in the CSP program as a 2-Tier reseller
The biggest changes for a typical O365 reseller will be owning the entire billing cycle, and taking on the entirety of the support for your tenants, instead of the tenants raising issues to Microsoft directly. This means you are going to need, if you want to be successful and grow your O365 CSP tenant offering, a 24/7 support team – primarily delivered over the phone.
So what are Microsofts expectations of a Cloud Provider signed up to the CSP?
Own and control the billing
- Provide customers with one consolidated bill, monthly or annually
- Order from a wholesale price list, create unique offers, and set the price
- Create financing options, such as spreading upfront costs over the fiscal year
Sell integrated offers and services
- Introduce service offers across each stage of the customer lifecycle
- Include your tools, products, or services in one integrated sales motion
- Increase upsell opportunity with greater customer touch points
Provision, manage, and support
- Directly provision and manage your customers' tenant with in-product tools
- Address customer technical support issues as admin-on-behalf
- Drive customer satisfaction as the first point of contact
This is all interesting stuff, the Microsoft focus appears to rely on the expertise of Cloud Providers knitting together an O365 support model and customer experience without Microsoft having to take the hit in the support cycle – we all know the apparent burden of O365 support on Microsoft and that raising tickets as an O365 customer hasn't provided the best experience. It makes sense that Microsoft are looking to de-emphasise support and most likely at the same time increase their revenue from the service.
One of the other immediate apparent benefits is the power and focus of automation for many Cloud Providers – O365 is great – but currently all products and services are Microsoft – with an active Cloud Provider with good standing relationships with many vendors I can foresee customers being able to purchase their O365 services and actually selecting other services in the service wrap – all automated, setup and integrated and hybridised by the Cloud Provider – with a single unified bill to the customer – fantastic.
Come back next week as we take an active look at the O365 Portal as a CSP enabled Partner. See you then!
Oliver Moazzezi - MVP Exchange Server